Secure Azure Virtual Machines using Just-in-time VM access: A step-by-step configuration guide

Cloud security is a major challenge for organizations running mission critical applications on cloud. One of the biggest risks from hackers come via open ports, and Microsoft Azure Security Center provides a great option to manage this threat – Just-in-Time VM access!
What is Just-in-Time VM access?
With Just-in-Time VM access, you can define what VM and what ports can be opened and controlled and for how long. The Just-in-Time access locks down and limits the ports of Azure virtual machines in order to overcome malicious attacks on the virtual machine, therefore only providing access to a port for a limited amount of time. Basically, you block all inbound traffic at the network level.
When Just-In-Time access is enabled, every user’s request for access will be routed through Azure RBAC, and access will be granted only to users with the right credentials. Once a request is approved, the Security Center automatically configures the NSGs to allow inbound traffic to these ports – only for the requested amount of time, after which it restores the NSGs to their previous states.
The just-in-time option is available only for the standard security center tier and is only applicable for VMs deployed via Azure resource manager.
What are the permissions needed to configure and use JIT?
| To enable a user to: | Permissions to set |
| Configure or edit a JIT policy for a VM | Assign these actions to the role: On the scope of a subscription or resource group that is associated with the VM: Microsoft.Security/locations/jitNetworkAccessPolicies/write On the scope of a subscription or resource group of VM: Microsoft.Compute/virtualMachines/write |
| Request JIT access to a VM | Assign these actions to the user: On the scope of a subscription or resource group that is associated with the VM: Microsoft.Security/locations/jitNetworkAccessPolicies/initiate/action On the scope of a subscription or resource group that is associated with the VM: Microsoft.Security/locations/jitNetworkAccessPolicies/*/read On the scope of a subscription or resource group or VM: Microsoft.Compute/virtualMachines/read On the scope of a subscription or resource group or VM: Microsoft.Network/networkInterfaces/*/read |
Why Just-in-Time access?
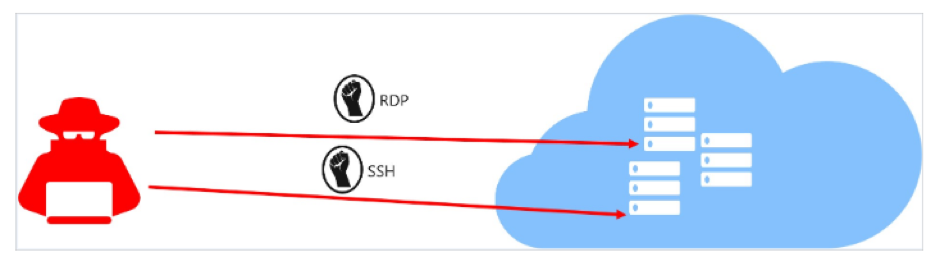
Consider the scenario where a virtual machine is deployed in Azure, and the management port is opened for all IP addresses all the time. This leaves the VM open for brute force attack.
The brute force attack is usually targeted to Management ports like SSH (22) and RDP (3389). If the attacker compromises the security, the whole VM will be open to them. Even though we might have NSG firewalls enabled in our Azure infrastructure, it’s best to limit the exposure of management port within the team for a limited amount of time.
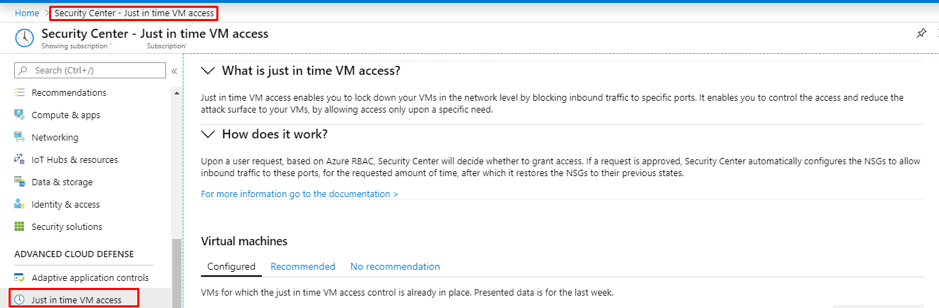
How to enable JIT?
Just-In-Time access can be implemented in two ways,
- Go to Azure security center and click on Just-in-Time VM
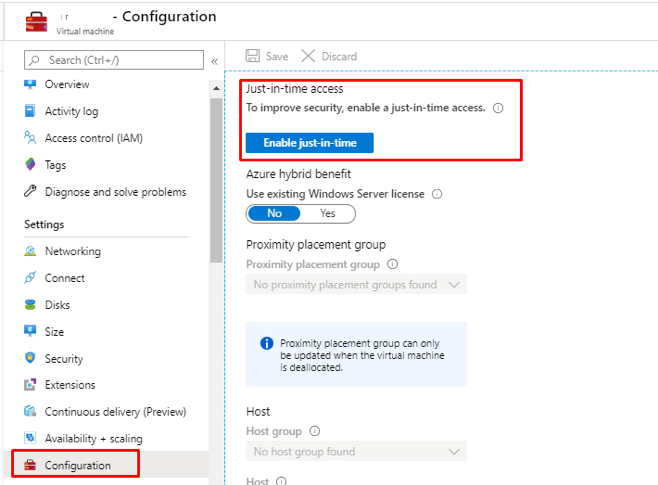
2. Go to the VM, then click on configuration and “Enable JIT”
How to set up port restrictions?
Go to Azure security center and click on recommendations for Compute &Apps.
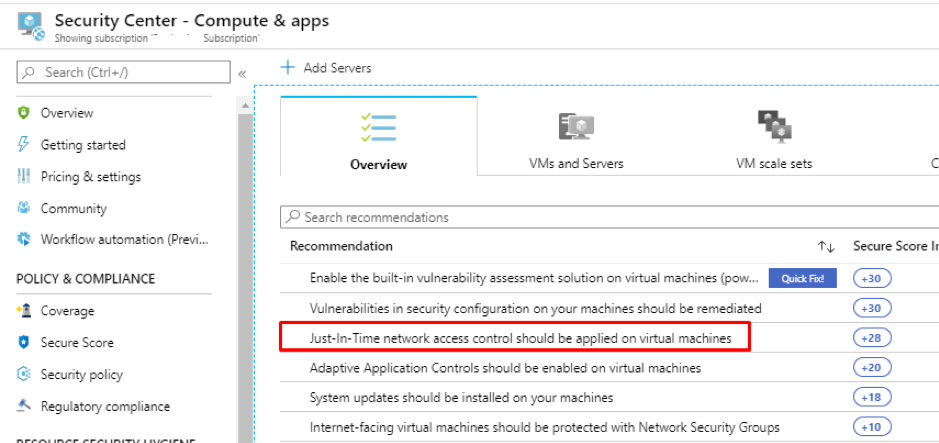
Select the VM and click Enable JIT on VMs.
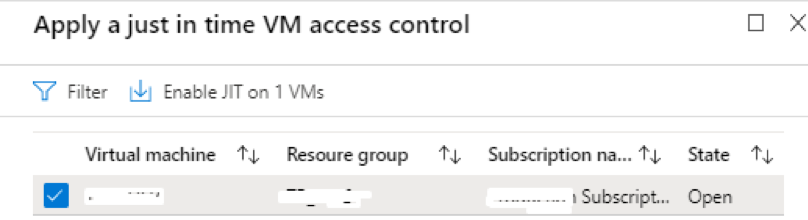
It will then show a list of recommended ports. It is possible to add additional ports as per requirement. The default port list is show below.
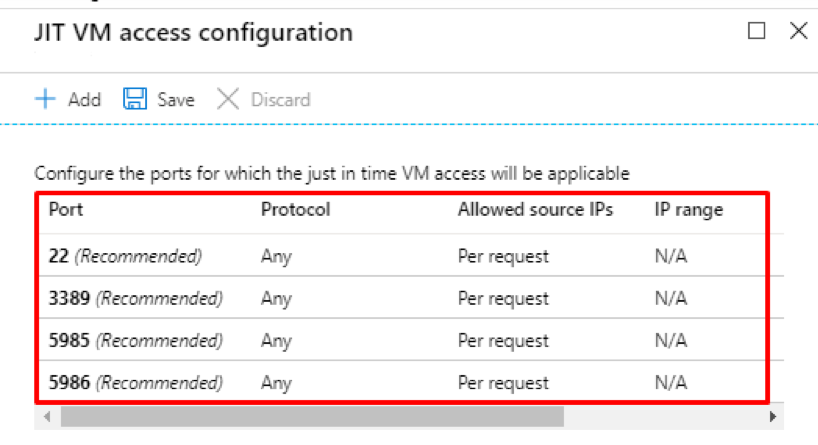
Now click on the port that you wish to restrict. A new tab will appear with information on the protocol to be allowed, allowed source IP (per IP address, or a CIDR range).
The main thing to note is the request time. The default time is 3 hours; it can be increased or decreased as per the requirement. Then click, OK.
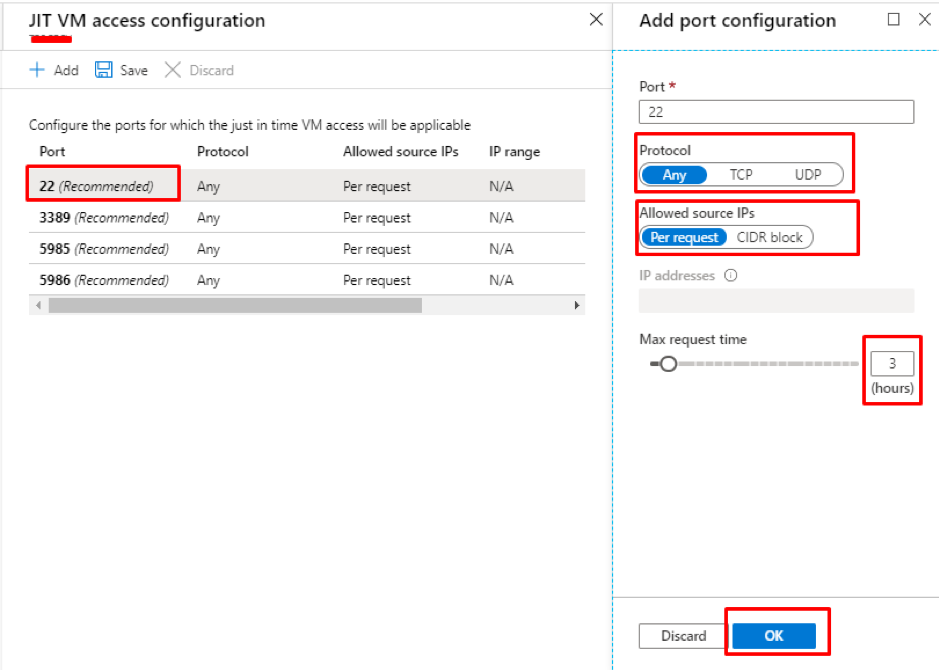
Click OK and the VM will appear in the Just-in-Time access window in the security center.
What changes will happen in the infrastructure when JIT is enabled?
The Azure security center will create a new Deny rule with a priority less than the original Management port’s Allow rule in the Network security group’s Inbound security rule.
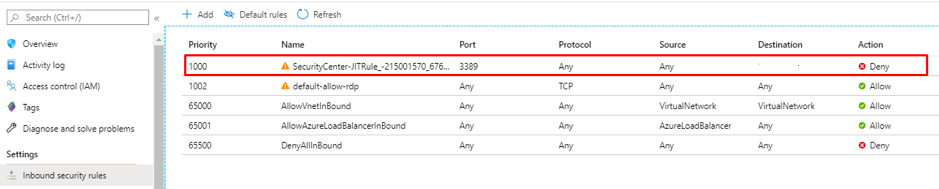
If the VM is behind an Azure firewall, the same rule overwrite occurs in the Azure firewall as well.
How to connect to the JIT enabled VM?
Go to Azure security center and navigate to Just-in-Time access.
Select the VM that you need to access and click on “Request Access”
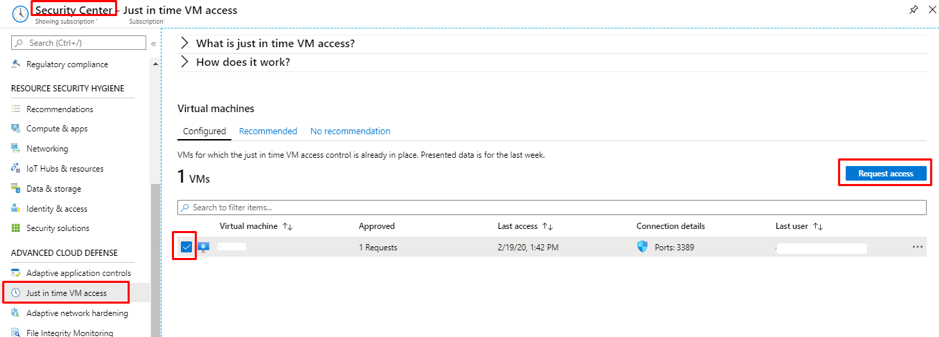
This will take you to the next page where extra details need to be provided for connectivity such as,
- Click ON Toggle
- Provide Allowed IP ranges
- Select time range
- Provide a justification for VM Access
- Click on Open Ports
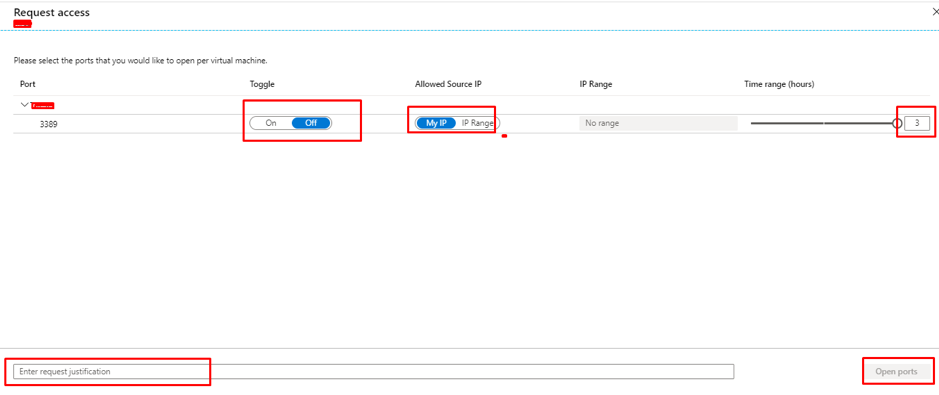
This process will overwrite the NSG Deny rule and create a new Allow rule with less priority than the Deny All inbound rule or the selected port.
The above-mentioned connectivity process includes two things
- IP Range
- My IP options
IP Range:
In this option, we can provide either a single IP or a CIDR block.
MY IP:
Case 1: If you’re connected to Azure via a public network, i.e., without any IP sec tunnel, while selecting MY IP, the IP address that is to be registered will be the Public IP address of the device you’re connecting from.
Case 2: If you’re connected to Azure via a VPN/ IP Sec tunnel/ VNET Gateway, you can’t possibly use MY IP option. Since the MY IP option directly captures the Public IP and it can’t be used. In this scenario, we need to provide the private IP address of VPN gateway for a single user, or to allow a group of users, provide private IP CIDR Block of the whole organization.
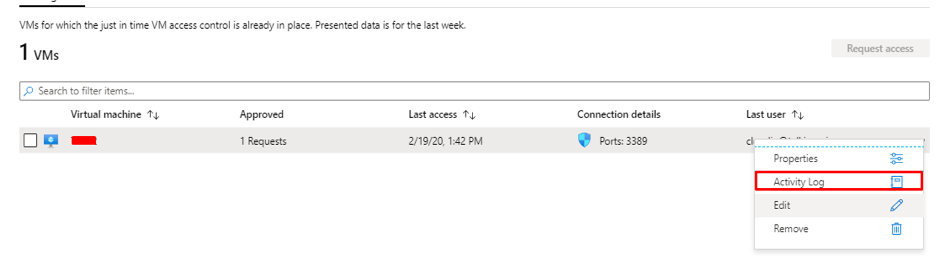
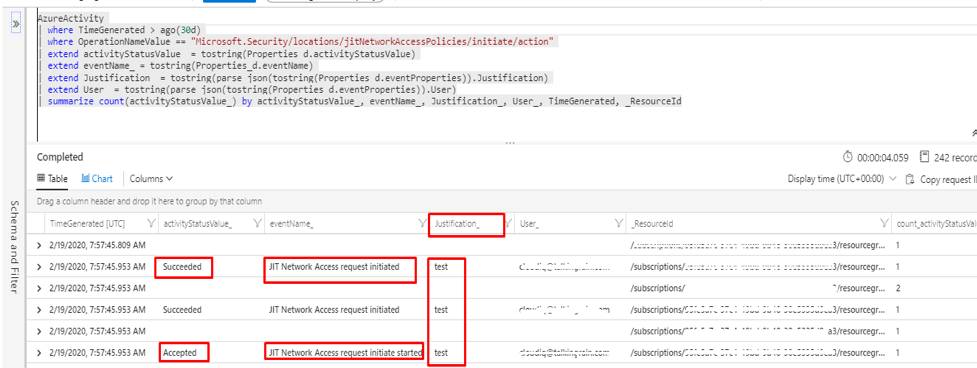
How to monitor who’s requested the access?
The users who request access are registered as Activity. To view the activities in Log analytics workspace, link the Subscription Activity to Log analytics.
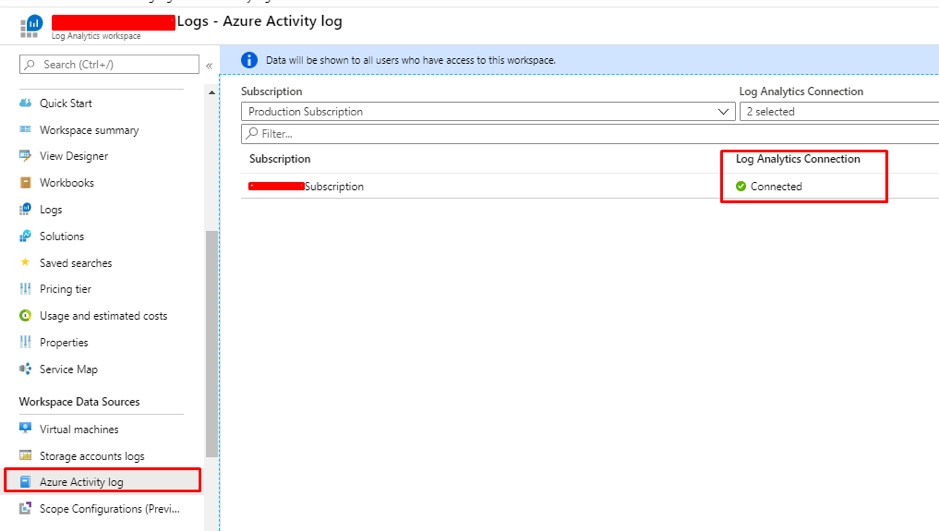
It is possible to view the list of users accessed in the log analytics workspace with the help of Kusto Query Language(KQL), once it is configured to send an activity log to log analytics.
Share this:

CloudIQ is a leading Cloud Consulting and Solutions firm that helps businesses solve today’s problems and plan the enterprise of tomorrow by integrating intelligent cloud solutions. We help you leverage the technologies that make your people more productive, your infrastructure more intelligent, and your business more profitable.
LATEST THINKING
INDIA
Chennai One IT SEZ,
Module No:5-C, Phase ll, 2nd Floor, North Block, Pallavaram-Thoraipakkam 200 ft road, Thoraipakkam, Chennai – 600097
© 2023 CloudIQ Technologies. All rights reserved.

