Creating AWS Security Groups for Kubernetes

In this article we will discuss how to create security groups in AWS for Kubernetes. The goal is to set up a Kubernetes cluster on AWS EC2, having provisioned your virtual machines. You are going to need two security groups: one for the control plane load balancer, and another for the VMs.
Creating a Security Group through the AWS Console
Prerequisite: You should have a VPC (virtual private cloud) set up.
Log into the AWS EC2 (or VPC) console. On the left-hand menu, under Network and Security, click Security Groups.
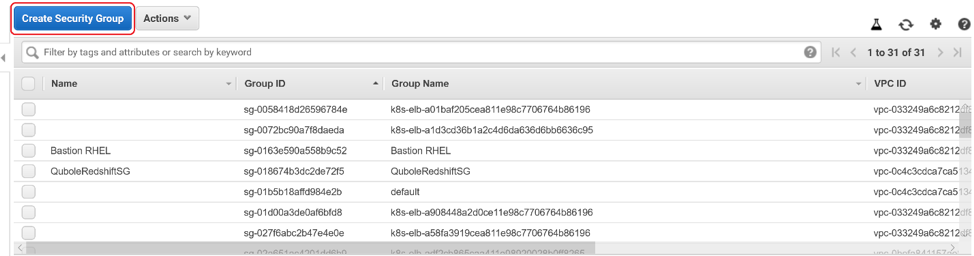
Click on Create Security Group.
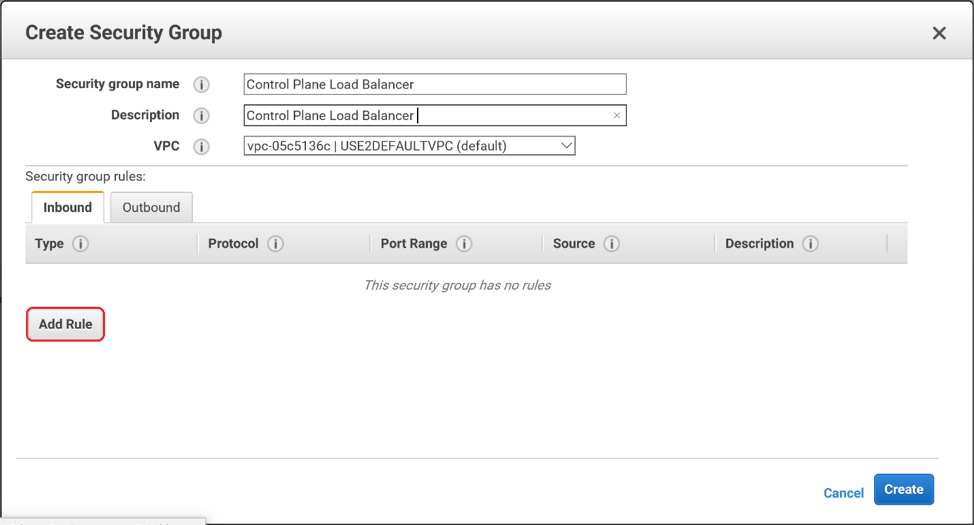
Enter a Name and a Description for your Security Group. Then select your VPC from the drop-down menu. Click Add Rule.
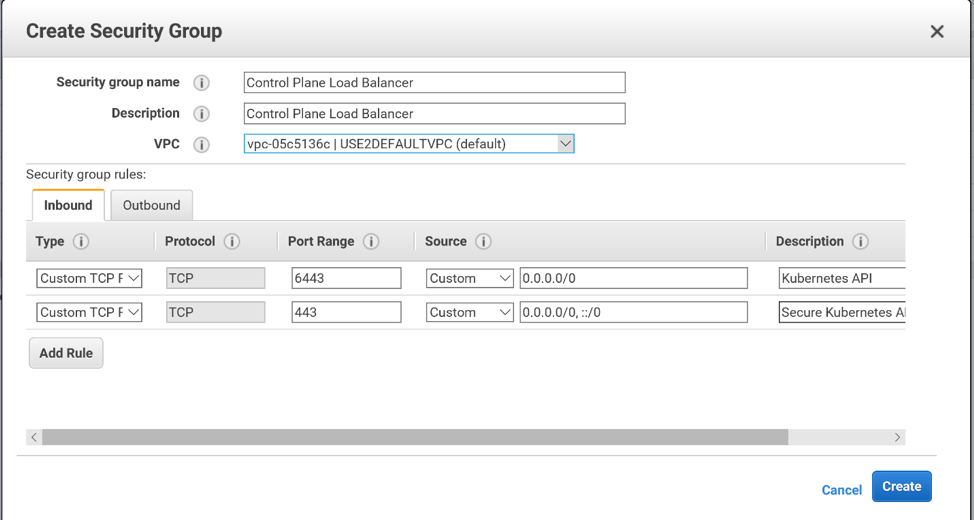
You will need 2 TCP ingress rules, one over port 6443, another over port 443. We are choosing to allow the Source from anywhere. In production you may want to restrict the CIDR, IP, or security group that can reach this load balancer.
We are choosing to leave the outbound rules as default, in which all outbound traffic is permitted.
Click Create and your security group is created!
Select your security group in the console. You may want to give your security group a Name (in addition to the Group Name that you specified when creating it).
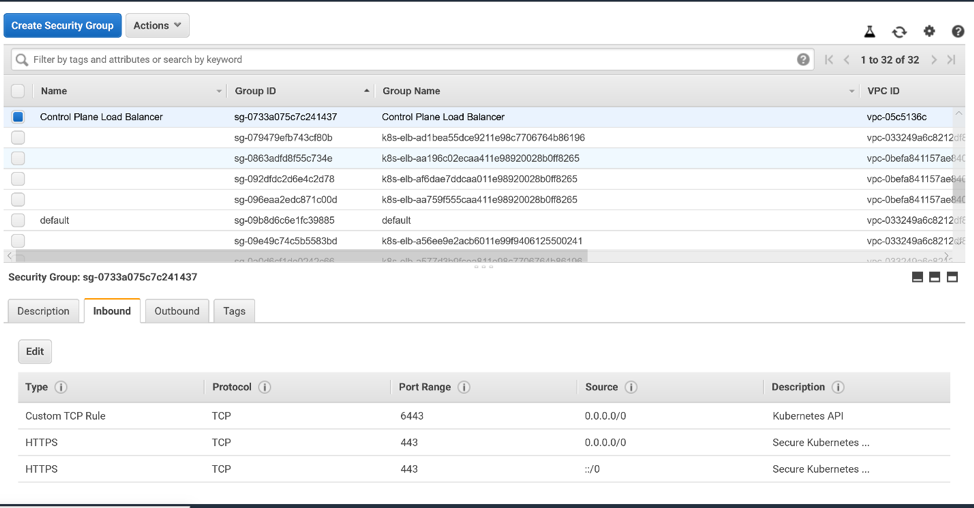
But you are not done yet: you must add tags to your security group. These tags will alert AWS that this security group is to be used for Kubernetes. Click on the Tags tab at the bottom of the window. Then click Add/Edit Tags.
You will need 2 tags:
- Name: KubernetesCluster. Value: <the name of your Kubernetes cluster>
- Name: kubernetes.io/cluster/<the name of your Kubernetes cluster>. Value: owned
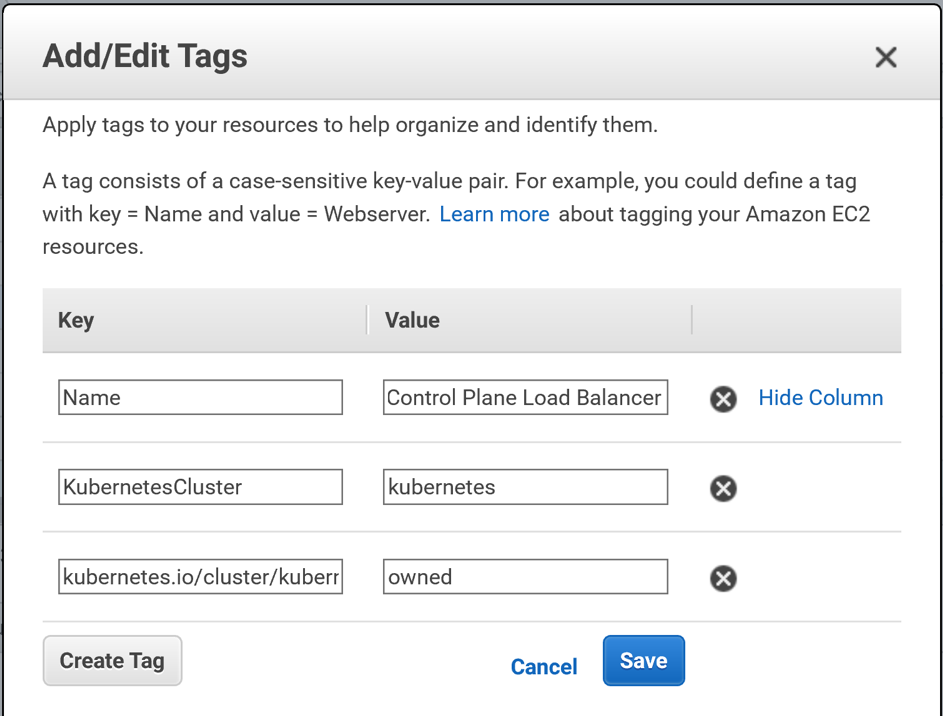
Click Save and your tags are saved!
Creating a Security Group for the Virtual Machines
Follow the steps above to create a security group for your virtual machines. Here are the ports that you will need to open for your control plane VMs:
The master node:
- 22 for SSH from your bastion host
- 6443 for the Kubernetes API Server
- 2379-2380 for the ETCD server
- 10250 for the Kubelet health check
- 10252 for the Kube controller manager
- 10255 for the read only kubelet API
The worker nodes:
- 22 for SSH
- 10250 for the kubelet health check
- 30000-32767 for external applications. However, it is more likely that you will expose external applications to outside the cluster via load balancers, and restrict access to these ports to within your vpc.
- 10255 for the read only kubelet API
We have chosen to combine the master and the worker rules into one security group for convenience. You may want to separate them into 2 security groups for extra security.
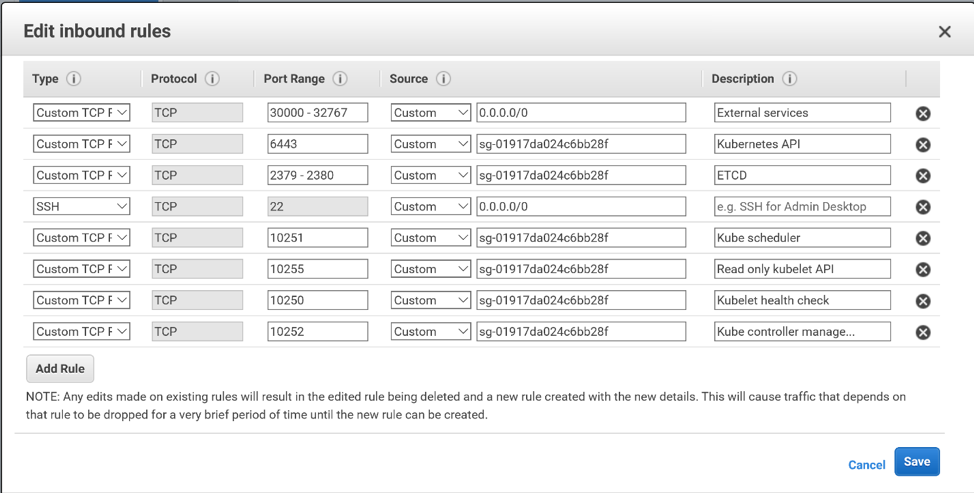
Follow the step-by-step instructions detailed above and you will have successfully created AWS Security Groups for Kubernetes.
Share this:

CloudIQ is a leading Cloud Consulting and Solutions firm that helps businesses solve today’s problems and plan the enterprise of tomorrow by integrating intelligent cloud solutions. We help you leverage the technologies that make your people more productive, your infrastructure more intelligent, and your business more profitable.
LATEST THINKING
INDIA
Chennai One IT SEZ,
Module No:5-C, Phase ll, 2nd Floor, North Block, Pallavaram-Thoraipakkam 200 ft road, Thoraipakkam, Chennai – 600097
© 2023 CloudIQ Technologies. All rights reserved.

